Overview
Our fully 802.11-compliant offerings imbue WLANs with the intelligence to identify devices and users as they connect; flawlessly adjust the level, confidentiality, quality and type of services being delivered; track and locate roaming connections and portable equipment; monitor for and safeguard against unauthorized machines, activity, sessions and users.
We deliver a “smarter” enterprise network infrastructure; one that unifies wired and wireless segments of the LAN, virtualizes data centers and frees users to roam like never before. This is achieved by greatly simplifing the task of mobilizing users, without compromising security or performance while supporting the most advanced wireless applications—including cross-subnet roaming, high-speed multicast, mobile voice or streaming multimedia.
Our designs support high-bandwidth, high-performance enterprise applications with Access Points ideal for delivering low-latency voice and video streams and bandwidth-greedy imaging files. All these by providing a wide selection of form factors answers just about any installation challenge—outdoor/indoor environments, surface/hidden mounts, high-/low-interference environments, remote/centralized management—and office sizes ranging from single telecommuters, to small branch campuses, to large headquarters.
The Service
“Unloading end systems from having to host resident applications lets mobile users travel light, without losing processing power, thanks to the latest generation of ultra-portable, browser-enabled, graphics-friendly tablets and smartphones.”
(Stavros, IS Senior Consultant)
We are able to offer WLAN Solutions designed to evolve enterprise networks to the new mobility model by enabling a wireless architecture that is device-agnostic, application-aware, easily scalable and transparently manageable.
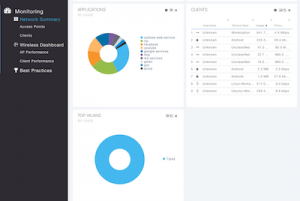
Our strengths in providing WLAN installation and configuration services are:
- Scalable Architecture – Plan, configure and deploy IT infrastructures to help achieve your business objectives. Our scalable WLAN architectures deliver enterprise-class features now, with plenty of options for future expansion. Choose integrated or overlay solutions, thin or adaptive access points, controller-based or centralized administration, role-, device- or location-based identity management, legacy compatibility, single, dual or triple radios, and much more.
- Multilayered Security – Our WLAN solutions provide comprehensive security against network threats, including shared key authentication, RADIUS/LDAP server, hardware encryption engine, hotspot authentication and redirect, MAC address filtering, wireless IDS/IPS, stateful packet inspection, IPSec VPN tunneling, sensorless rogue detection, heuristic and forensic reporting, proactive alerting, browser-based management consoles and more.
- Secure Guest Access – Guest user or hotspot authentication offers secured public access that won’t expose internal networks and servers. Guest user logins are captured and redirected to a captive portal login page that identifies and validates user credentials before granting access.
- High Availability – Resilient, fault-tolerant controller clusters support 1:N redundancy, load-balancing, traffic prioritization, license sharing, AP redirection and automated failover. AP mesh configurations help eliminate traffic hairpins and congestion for high-density user access. Self-Monitoring at Run Time Radio Frequency (SMART RF) senses and adjusts power levels and signal strength for changing transmissions distances, RF interference and hardware failure.
- Toll-Quality, Wireless Voice – Multiple-input, multiple-output (MIMO) antenna arrays and dual-frequency bands (2.4 GHz/5GHz) provide wired-like throughputs and signal clarity. 802.11e Quality of Service (Qos), Wi-Fi Multimedia (WMM), Unscheduled Automatic Power Save Delivery (UAPSD), SIP Call Admission Control and SMART RF optimize delivery of time-sensitive traffic, such as IP PBX telephony and multicast video.
- Design and Deployment – Deploy our WLAN solutions anywhere in the network with easy integration into your existing topology. For pre-installation site surveys, specialized software helps determine optimal installation and configuration of WLAN hardware, and takes into account existing infrastructures, RF environments, user densities and service types and quality.
- Monitoring and Management – We use WLAN service platforms that work like a virtual IT assistant to remotely monitor, configure and troubleshoot wireless environments across the entire campus, including remote locations. Control consoles delivers real-time visibility into and control of a wireless infrastructure comprised of hundreds of APs and thousands of disparate client devices.
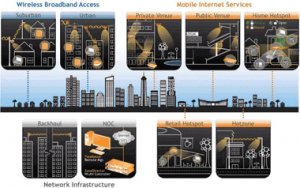
Approach
The deployments of our WLAN solutions help resolve traditional network challenges, such as:
- Installing seamless, mobile connectivity across multiple locations thus giving mobile users reliable access to network services and data regardless of where they go, including temporary sites, branch offices and remote campuses.
- Ensuring clear transmissions in mixed RF environments to minimize network lag time and maintain QoS for mobile devices sharing airspace already crowded with wireless signals from 802.11, 3G/4G, microwave, Bluetooth, HIPERLAN, and other RF fields.
- Delivering voice, video and imaging to hard-to-wire locations by distributing toll-quality voice, real-time video and interactive media to outdoor sites such as college campuses, construction sites, sports stadiums and solid-walled structures such as elevator shafts, parking garages, brick buildings.
- Deploying cost-effective, future-proofed infrastructures to maximize capital IT investments with standards-based architectures, device-independent interoperability, backwards-/forwards-compatibility, remote manageability, plug-and-play installation and easy wired-to-wireless integration.
- Enforcing multi-tiered security that protects data, users and networks by adding multiple layers of protection—including authentication, encryption, activity monitoring, intrusion detection/prevention and sensorless scanning—that follow mobile connections across decentralized data centers, and wired and wireless infrastructures.

